Sumvin ID Litepaper
Verified Identity Infrastructure for the Agentic Economy
Abstract
Sumvin ID is a decentralized identity infrastructure that enables privacy-preserving verification for AI agents operating on behalf of verified users. The system combines an immutable on-chain identity anchor with transient cryptographic proofs, allowing merchants to verify user attributes without receiving sensitive personal data. This document describes the architecture, credential structure, verification protocols, and integration pathways for the Sumvin ID system.
1. Introduction
1.1 The Identity Problem in Agentic Commerce
The emergence of AI agents as autonomous financial actors introduces a fundamental trust problem. When an agent initiates a transaction, the receiving merchant must answer three questions that existing identity infrastructure cannot address:
Proof of Personhood: Is there a real, KYC-verified human behind this agent, or is this synthetic traffic from an unverified source?
Proof of Authorization: Has this specific person explicitly authorized this specific agent to perform this specific action?
Proof of Attributes: Does this person meet the compliance requirements for this transaction (age, jurisdiction, KYC status) without requiring the merchant to collect and store sensitive documents?
Traditional identity verification assumes human presence at the point of interaction. Document upload, liveness checks, and form completion all require a person at the keyboard. AI agents break this assumption, creating a gap between merchant compliance requirements and the technical reality of agent-initiated transactions.
1.2 Design Goals
Sumvin ID is designed around four core objectives:
User Sovereignty: Users own their identity credentials and control exactly what information is shared, with whom, and under what circumstances. No transaction occurs without explicit user authorization.
Privacy by Default: Personal data should not leave the user's control unless absolutely necessary. Merchants should be able to verify claims about users without receiving the underlying data.
Cryptographic Verifiability: All claims must be independently verifiable by merchants without requiring trust in Sumvin as an intermediary. Verification should be possible using only public information and published cryptographic methods.
Delegated Authority: Users must be able to grant their AI agents well-defined, auditable, and revocable authority to act on their behalf.
2. Architecture Overview
The Sumvin ID system consists of five primary components that work together to issue, manage, and verify identity credentials.
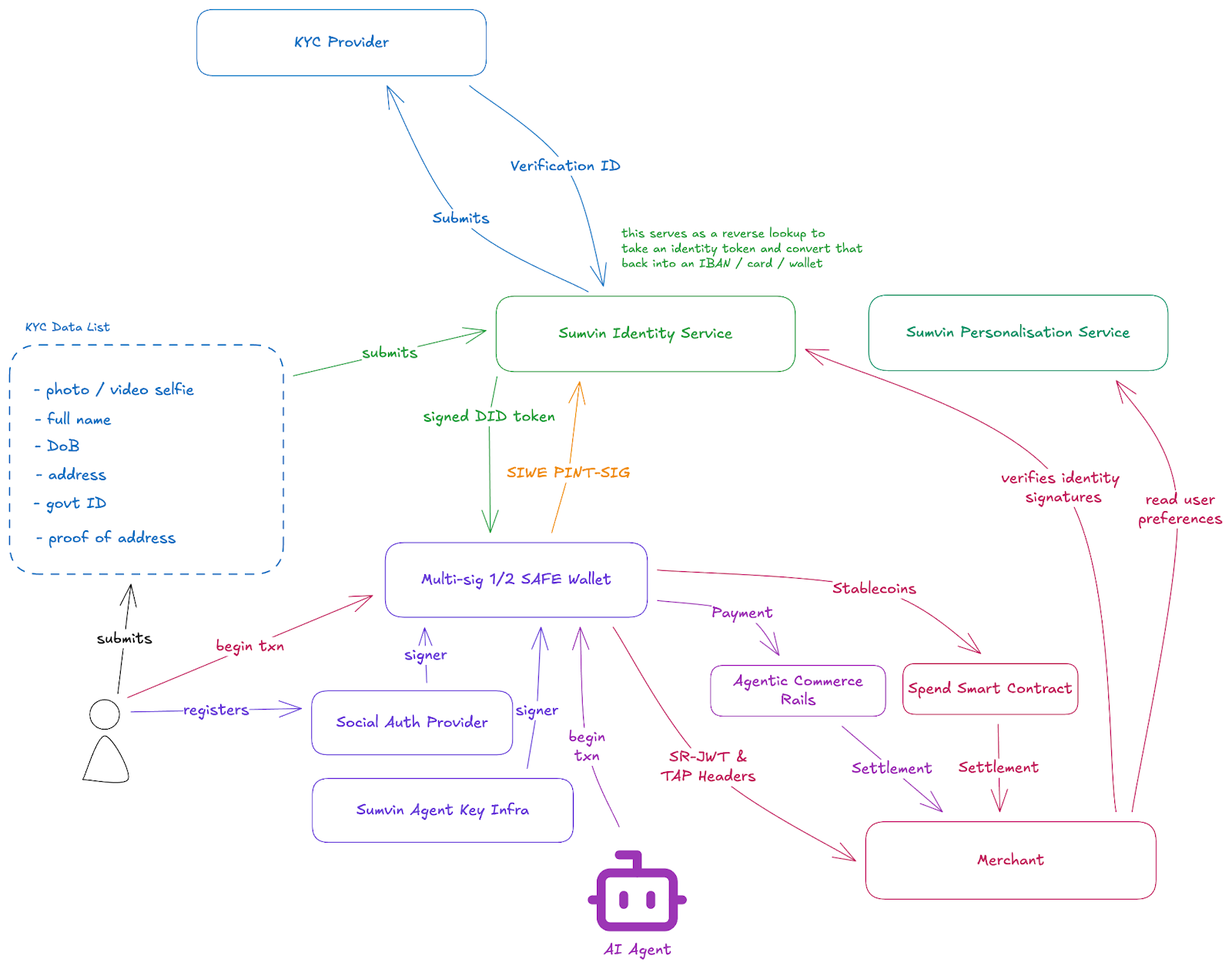
2.1 Component Summary
Sumvin Identity Service (SIS) serves as the central orchestrator for identity operations. It coordinates KYC verification, issues identity credentials, generates cryptographic proofs on demand, and enforces user privacy preferences when merchants request data.
Smart Account Wallet is a multi-signature wallet issued to each user, secured by a one-of-two signature scheme. Both the user and their authorized AI agent hold signing keys, enabling either party to authorize transactions while maintaining clear audit trails of who signed each action.
On-Chain Identity Anchor is an immutable credential stored on-chain that contains cryptographic commitments to the user's verified attributes. This anchor stores no personal data—only hashes that serve as fixed reference points for future proof verification.
Proof Generation Service operates within the SIS to generate privacy-preserving proofs on demand. When a merchant requires verification of a specific claim, this service produces a cryptographic proof that attests to the claim without revealing the underlying data.
Sumvin Personalisation Service manages user preferences and marketing data for authorized partners who wish to personalize their offerings. Access requires explicit user consent encoded in the authorization.
3. Identity Credential Structure
Each Sumvin ID comprises two linked components: a persistent on-chain anchor and transient proof tokens issued for specific interactions.
3.1 Sumvin Resource Identifier (SRI)
Every user receives a unique, parsable identifier that encodes their credential type and wallet address:
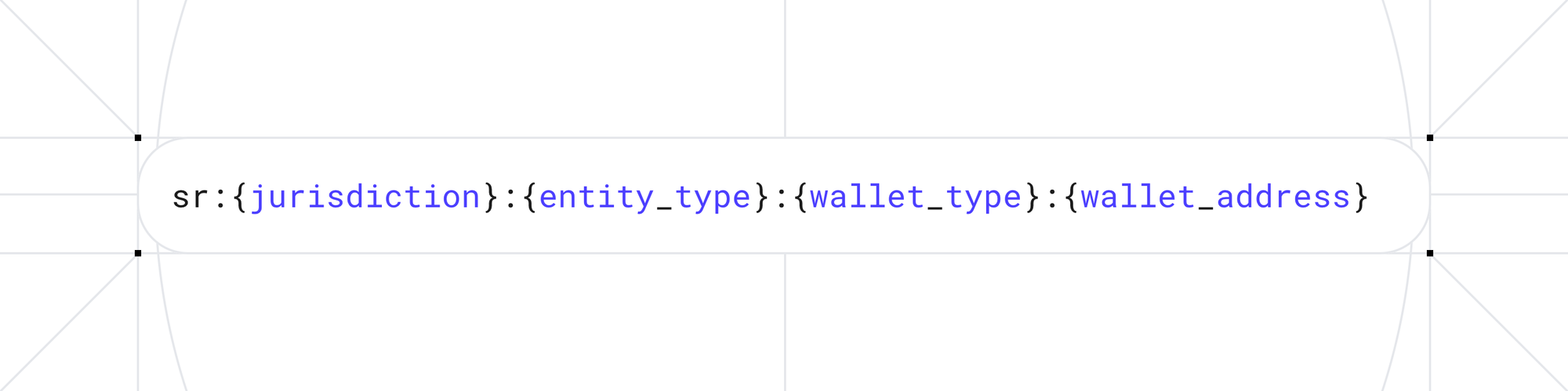
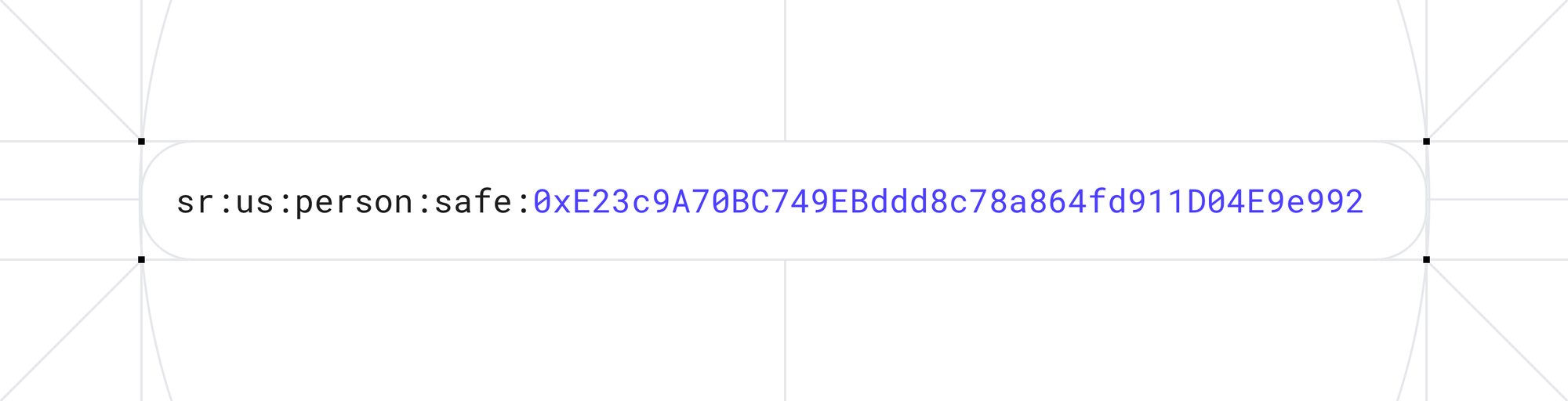
This identifier allows merchants to deterministically understand which user they are transacting with and locate the corresponding on-chain anchor for verification.
3.2 On-Chain Identity Anchor
The on-chain anchor is a non-transferable credential minted to the user's wallet upon successful KYC verification. It contains cryptographic commitments—one-way hashes of the user's verified attributes combined with unique salts—but never the attributes themselves.
These commitments serve as fixed reference points. When Sumvin generates a proof that a user is over 18, the proof includes a commitment value that must match the commitment stored on-chain. This binding ensures proofs cannot be forged or transferred between users.
The anchor is immutable once minted. If a user's KYC status is revoked, the anchor is burned and a new verification is required.
3.3 Transient Proof Token
When a user or agent initiates an action requiring identity verification, the SIS issues a short-lived signed token containing the relevant proofs. This token follows standard JWT conventions (RFC 7519) and includes:
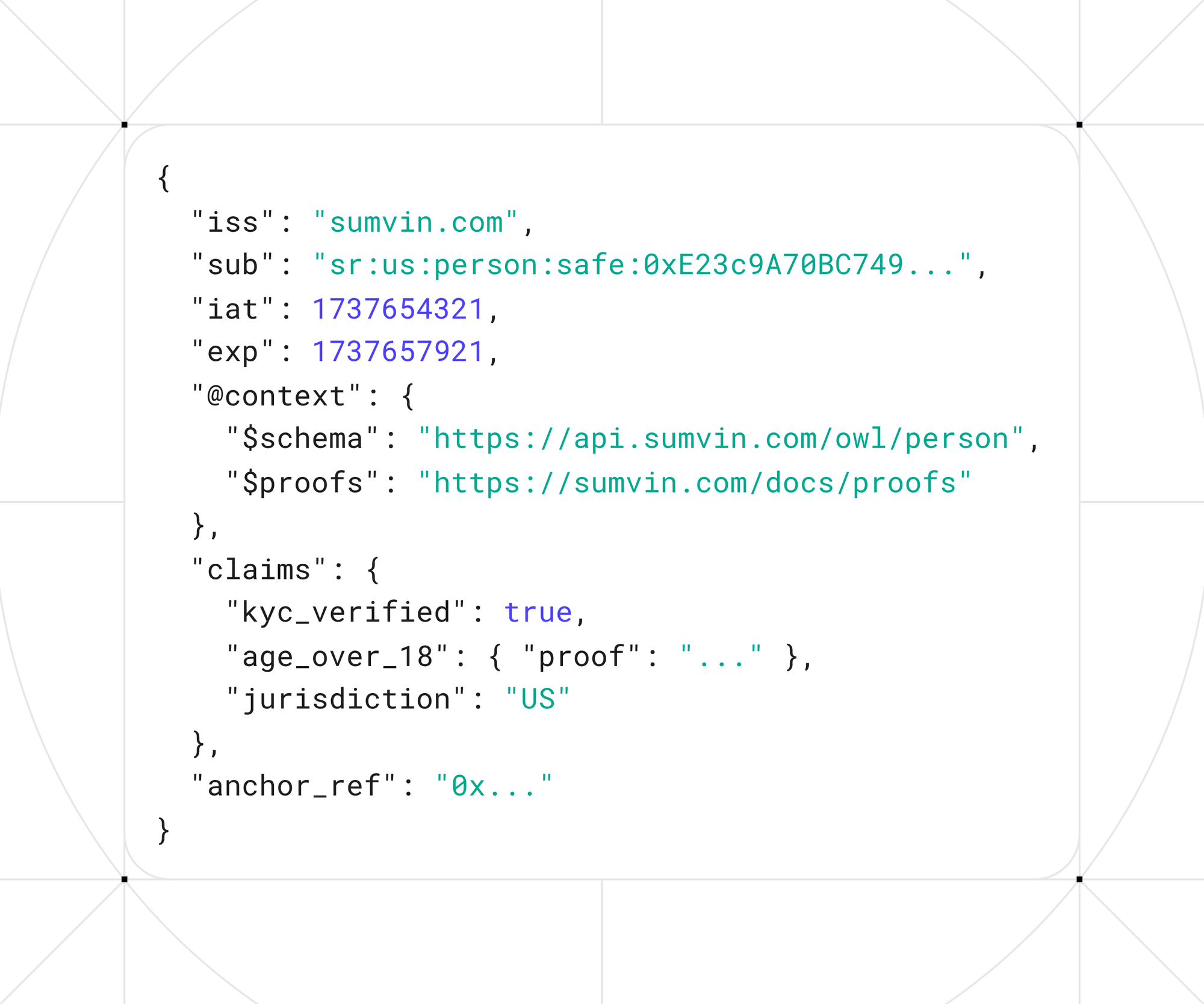
The token is signed by Sumvin's identity service and references the user's on-chain anchor. Merchants verify the signature, validate the proofs, and confirm the proof commitments match the on-chain anchor.
4. Authorization Model
4.1 Dual-Key Architecture
The Smart Account Wallet employs a one-of-two multi-signature scheme with two distinct key pairs:
User Key is derived from social authentication or passkey-based cryptography, providing familiar login experiences while maintaining non-custodial security. Users access their key through established authentication flows (social login, biometrics, hardware keys).
Agent Key is held by the user's authorized AI agent within Sumvin's secure key infrastructure. This key allows the agent to sign transactions and authorizations when operating autonomously on the user's behalf.
Either key can independently authorize actions from the shared wallet. However, the signature clearly identifies which party signed, creating an auditable record of whether the user or agent initiated each action.
4.2 Purchase Intent (PINT)
All agent-initiated actions requiring identity verification flow through the Purchase Intent protocol. A PINT represents explicit authorization from the user for a specific action.
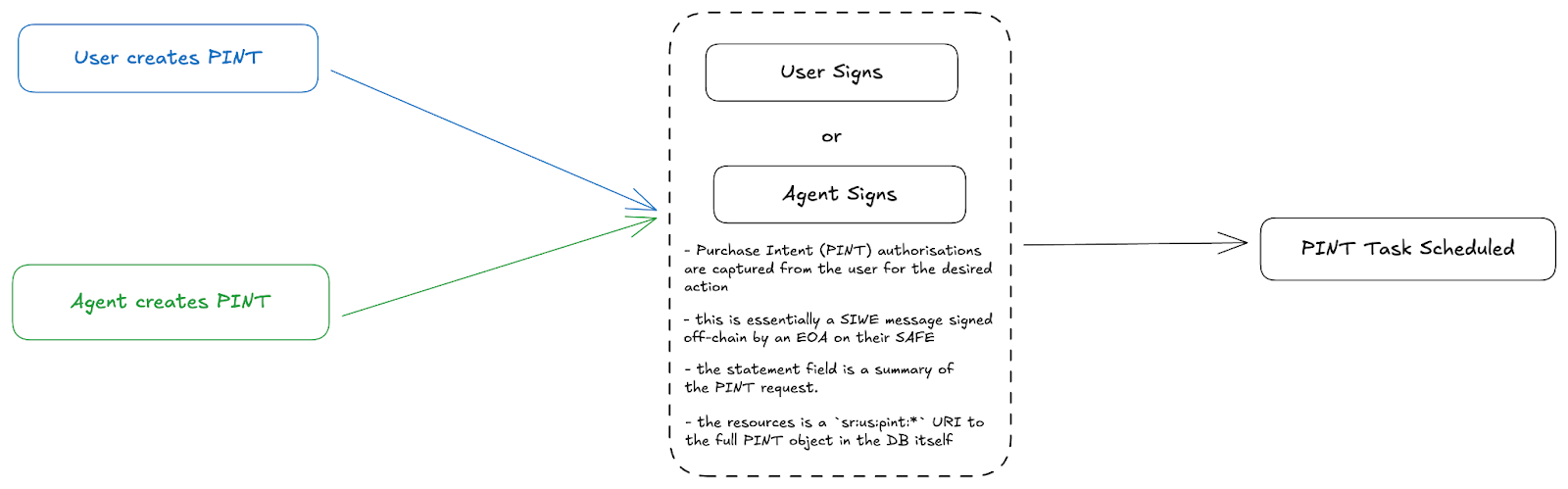
The PINT comprises two components:
Intent Object contains the full details of the authorized action: merchant, scope, amount limits, expiration, and any constraints on execution.
Authorization Signature is a Sign-In-With-Ethereum (SIWE) message signed by either the user or agent key, cryptographically binding the authorization to the user's identity and wallet.
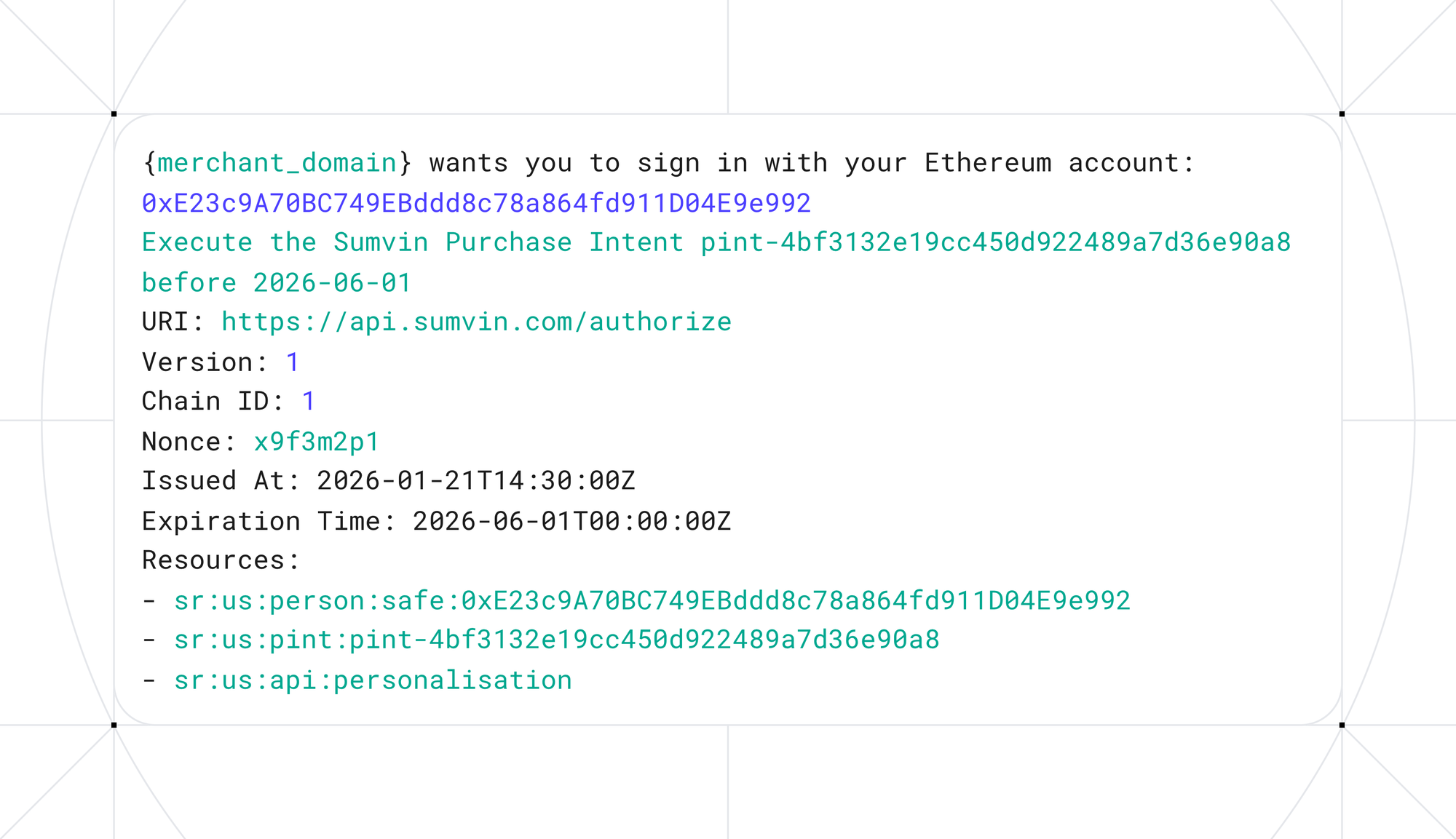
The resources array explicitly enumerates the scopes granted for this intent, including identity usage, the specific PINT reference, and any optional API access.
5. Verification Protocol
When an AI agent interacts with a merchant on a user's behalf, the merchant can verify identity through a progressive assurance model. Each tier provides stronger guarantees while requiring additional verification steps.
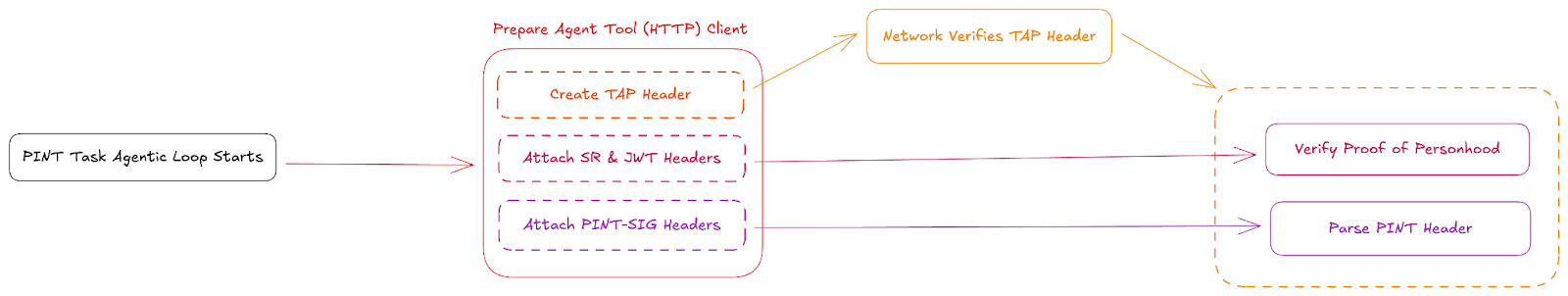
5.1 Tier 1: Trusted Agent Verification
The agent includes a Trusted Agent Protocol (TAP) header with each request. This header attests that the traffic originates from a verified agent within the Sumvin ecosystem.
Merchants validate the TAP header at the network layer to confirm the request comes from legitimate agent infrastructure rather than unverified automation. This provides baseline protection against bot traffic and synthetic requests.
Verification: Cryptographic signature validation against Sumvin's published TAP signing keys.
5.2 Tier 2: Proof of Personhood
The agent presents the transient proof token containing cryptographic proofs of specific claims. The merchant performs three verification steps:
- Signature Verification: Confirm the token was issued and signed by Sumvin's identity service using published verification keys.
- Proof Verification: Validate the cryptographic proofs themselves using published verification methods. The proofs are constructed such that they can only be valid if the underlying claim is true.
- Anchor Binding: Retrieve the user's on-chain identity anchor (referenced in the token) and confirm the proof commitments match the commitments stored on-chain. This binding prevents proof reuse across different users.
Verification: Local cryptographic verification using published keys and on-chain data. No Sumvin API calls required.
5.3 Tier 3: Verified Partner Data Access
Authorized partners who have completed Sumvin's onboarding process and established appropriate data handling agreements can request additional user data through the SIS API.
The partner presents the proof token along with their API credentials. Sumvin verifies the token, confirms the PINT authorizes this partner for data access, applies user privacy preferences, and returns the permitted data.
Verification: API call to Sumvin Identity Service with partner authentication.
5.4 Tier 4: Full KYC Relay
For regulated scenarios where partners must perform their own KYC (duplicate verification requirements, regulated financial services), Sumvin can relay the original verification data from the KYC provider.
This data is end-to-end encrypted with a pre-shared key between the KYC provider and the receiving partner. Sumvin facilitates the relay but cannot decrypt the contents, ensuring sensitive documents remain protected in transit.
Verification: Encrypted data relay through Sumvin with direct partner-to-KYC-provider key exchange.
6. Agent Execution Flow
When a PINT is ready for execution, the agent follows a structured flow to present the user's identity to merchants.
6.1 Pre-Flight
Before execution, the system validates rate limits, billing compliance, and policy checks against the user's account. The PINT is scheduled in a first-in-first-out queue with automatic termination at the signature expiration time.
6.2 Request Configuration
The agent's HTTP client is automatically configured with the required headers for the interaction:
TAP Header contains the signed attestation of the agent's verified status within the Sumvin ecosystem.
Identity Token Header carries the transient proof token with relevant claims for this merchant.
PINT Signature Header includes the SIWE authorization demonstrating user consent for this action.
6.3 Merchant Interaction
The agent executes the authorized action. The merchant receives the headers and performs verification appropriate to their requirements. Upon successful verification, the merchant processes the request and settles any resulting transactions through the configured payment rails.
7. Integration
7.1 Merchant Integration
Merchants integrate Sumvin ID verification through HTTP header inspection and optional API calls. The integration surface is minimal:
Header Parsing: Extract TAP, identity token, and PINT headers from incoming requests.
Local Verification: Validate signatures and proofs using published verification keys and methods. Reference implementations are available for common platforms.
On-Chain Verification: Query the user's identity anchor to confirm proof-to-anchor binding. Standard blockchain RPC calls to supported networks.
API Integration (optional): For Tier 3+ verification, integrate with the Sumvin Identity Service API to request additional user data with appropriate authorization.
7.2 Platform Integration
Platforms wishing to embed Sumvin ID capabilities into their own products can integrate at a deeper level:
White-Label KYC: Embed Sumvin's verification flow within your own onboarding experience.
Credential Issuance: Issue Sumvin-compatible credentials for users verified through your existing KYC processes.
Agent Infrastructure: Connect your AI agents to Sumvin's authorization and identity infrastructure.
8. Security Considerations
8.1 Data Minimization
Raw personal data is retained only where legally required and operationally necessary. KYC documents are processed, used to generate cryptographic commitments, and purged from working memory. Encrypted witnesses for proof generation are stored with per-user envelope encryption and accessed only transiently during proof computation.
8.2 Credential Revocation
If a user's KYC status is invalidated or they request credential revocation, the on-chain anchor is burned. All proofs reference the anchor, so burning immediately invalidates all outstanding proofs. No complex revocation lists or proof updates are required.
8.3 Key Security
User keys are non-custodial and backed by social recovery or hardware security modules. Agent keys are held in secure enclaves within Sumvin's infrastructure with strict access controls and audit logging. The one-of-two signature scheme ensures no single key compromise can drain user assets.
8.4 Proof Security
Cryptographic proofs are constructed using established zero-knowledge techniques that are computationally infeasible to forge. Proofs are bound to specific on-chain anchors, preventing transfer or reuse. Short token expiration limits the window for replay attacks.
9. Conclusion
Sumvin ID provides the identity infrastructure necessary for AI agents to participate in regulated commerce. By combining persistent on-chain anchors with transient privacy-preserving proofs, the system enables merchants to verify user attributes without accumulating sensitive personal data.
The architecture supports progressive assurance levels appropriate to different merchant requirements, from lightweight bot protection through to full KYC relay for regulated financial services. Users maintain sovereignty over their identity and grant explicit, auditable, revocable authorization for each agent action.
We invite merchants, platforms, and infrastructure providers to explore integration with Sumvin ID. For technical documentation, partnership inquiries, or pilot program participation, contact us
Appendix A: Glossary
Identity Anchor: Immutable on-chain credential containing cryptographic commitments to user attributes.
PINT (Purchase Intent): Explicit authorization object signed by user or agent granting permission for a specific action.
Proof Token: Short-lived JWT containing cryptographic proofs of specific claims about a user.
SIS (Sumvin Identity Service): Central service coordinating identity operations, proof generation, and data access.
SRI (Sumvin Resource Identifier): Unique parsable identifier for users, intents, and other system resources.
TAP (Trusted Agent Protocol): Header protocol attesting that traffic originates from verified agent infrastructure.
© 2026 Sumvin. All rights reserved.